Monsterpiece Theater Presents: Security Theater
In Cybersecurity we undermine our own case by confusing real security with security theater.

We've all seen security theater - and probably called it out - at some point in our own lives. Whether it is being told to take off our shoes in order to be scanned for boarding an airplane to the idea that you're safer at home with a handgun than without, or even car alarms we've all seen supposed "security measures" that at best are some sort of psychological reassurance and at worst a significant inconvenience that degrades us our experience.
Cybersecurity Theater
This sort of theater seeps into Cybersecurity as well. and when cybersecurity professionals engage in security theater we undermine our own efforts and position. Here are a few examples:
Compliance As Security
Compliance is important. Being non-compliant with international, federal, state, local, or even industry requirements is a business risk, and I encourage every company that is subject to such security and privacy related regulations to take appropriate measures to comply with them. However, compliance with them is not enough to ensure a secure environment.
For example, in this day and age being PCI Compliant is much more likely to mean you've figured out how to "outsource" your payment card activities than it indicates you've taken the time to secure your environment. Companies like Toast, Square, and others have taken the vast majority of PCI compliance requirements out of the hands of retailers, which is excellent news if you're such a vendor. This means that the rest of the retailer's environment is unregulated, and may or may not actually be secured.
If your cybersecurity agenda (or sales pitch) is built on compliance you're doing yourself a disservice - you're simply making it even harder to adopt good security controls and practices.
Frequently Changed Complex Passwords
Hold on. I can already hear the naysayers on this one. "Complex passwords are really important, and you never know when someone will have gotten hold of a password database." Both parts of that statement are trueish, but these days we know better.
Any single-factor authentication methodology is demonstrably insecure these days, and should be combined with a second factor. (brush up on multi-factor authentication here) We also know that changing passwords frequently is actually a burden on users, and leads to bad password habits, like reusing passwords across multiple sites and systems, using passwords that are little different from the previous password, and choosing easily guessable "leet-speak" passwords where things like exclamation points are used in place of the letter "I" or the number "1" in well understood patterns. Even worse, they lead to the dreaded "post-it-note" password memory process, let alone the cost associated with password resets when people have forgotten on Monday the password they changed on Friday. (Even I've done that one).

In fact, NIST's password guidance identifies length over complexity as most important, and even recommends using memorable (but private) passwords/passprhases (yes, the space character is now very appropriate though many systems can't handle them in a password), discourages the requirement to use numbers and special characters, and further discourages frequent changes.
So really MFA is considered relatively secure, and long (not necessarily complex) passwords are part of that recipe. Believe me, your users will prefer longer, easier to remember passwords that they don't have to keep changing, especially when combined with an easy to use MFA solution that operates smoothly.
SMS and Email Security Codes are Strong MFA
Simply put, no they are not. They're the absolute bare minimum of MFA options when paired with a password. In late 2024 CISA explicitly recommended moving away from SMS based MFA solutions. That same guidance recommended MFA solutions other than email as preferred as well. A large part of the issue is that neither SMS nor email are end-to-end encrypted, and are therefore subject to interception. Further cellular cloning and email account takeover are so common these days as to render both SMS and email based MFA ineffective.
Conflating Bad Metrics With Cybersecurity
I don't really care what your SOC ticket open/close statistics are, what security issues did they really represent?
I don't care how many TB of logs you've collected, what value did you get from them?
I don't care how many of your users did or didn't fall for the phishing test email, how many real phishing/BEC events happened and how did you adjust your tools to prevent the next one?
I don't care that you haven't declared an incident all year - I'd rather see effective responses to several incidents.
This is a difficult category of Cybersecurity Theater, and I'm not really sure I can tell you what to do instead of these. Every statistic or trend line I can suggest monitoring is dubious here, and the reason for it is core to what cybersecurity is all about: preventing or recovering from an incident. The problem here is that it is extremely difficult to "prove a negative," meaning that you can always prove you didn't detect an incident, but you can't necessarily prove there wasn't one.
I know, the board wants easily digestible statistics and trends. My best advice is to work with them to understand their expectations from your security program, work to understand what your program really does and can do, and track to those metrics while being clear about what those metrics don't say about your program. Though I will suggest one critical metric: security tool coverage. Are your security tools installed, configured, and reporting back from ALL of your IT devices? What are you doing to improve that statistic? This is one of the most meaningful technical control monitors I've ever encountered.
Taking the Theater Out of Cybersecurity
Whether we're practitioners, sellers, or security executives we can all make a meaningful effort to reduce and eliminate cybersecurity theater as we work. In my experience there are some good starting points for addressing this in our daily work.
Admit That There Is No Silver Bullet
Overblown claims are a real source of distrust and cynicism at every level in the cybersecurity ecosystem. Whether it's the CISO using bad faith tactics to convince the CFO and peers to spend more on cybersecurity, or the seller claiming that this next new technology will eliminate all your organization's cybersecurity shortcomings, this happens every day.
Metrics can help better quantify the real-world impact of a new cybersecurity engagement, product, or solution but as we just discussed those can be a theater of their own. Case studies, peer experience, and setting realistic expectations of a level of improvement are crucial to improving faith and trust from our stakeholders.
Understand the Problem Before Proposing a Solution
So much of cybersecurity theater comes from not really understanding the problem being solved for, and throwing the wrong solution into the mix. I'm reminded of an old WW-2 story about analysis done on allied bombers that were returning home after taking damage.
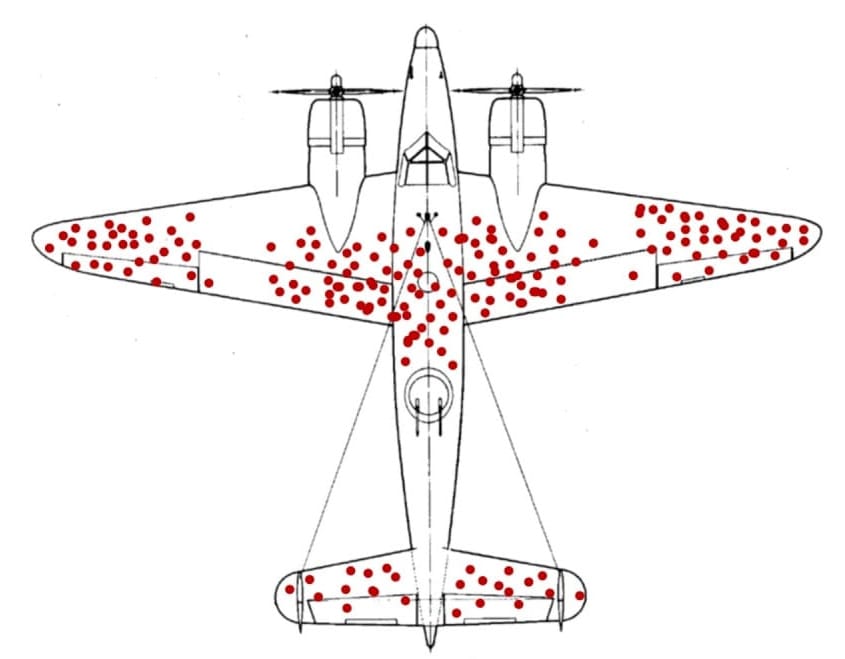
It seemed that there was a significant pattern to the damage inflicted on bombers that returned to Allied bases after attempting their missions. That analysis was interpreted to suggest that the damaged areas needed to be reinforced.
Fortunately, before time and money was spent on changing the bombers, a bright spark named Abraham Wald realized the flaw in the analysis, namely that the real lesson of this data was that bombers could sustain damage in these areas and still survive. Bombers that were damaged in the areas other than those identified in the analysis were the ones that didn't make it back to base, and the updated armor was really needed in those places instead: the cockpit, engines, and other areas.
Really understanding the problem you propose to solve for can help ensure a credible solution, and remove another layer of theater from your cybersecurity program, because sometimes even legitimate security controls can be cybersecurity theater if they're not the right controls for the situation.
Re-evaluate Your Own Theater
Did you (or your predecessors) deploy a DLP system that does nothing but frustrate your users? Are you still expecting your users to read and sign a 40 page cybersecurity policy document written in fluent legalese any more thoroughly than they read a software EULA on their smartphone? Is your anti-phishing program still suggesting that good spelling and grammar are indicators of legitimate email? If you answered "yes" to any of these questions - or are answering yes to any hypotheticals running around in your own head along these lines - then you need to come to terms with the theater in your own program. Identifying and addressing your own program's theater will go a long way toward improving your credibility across your organization.
As cybersecurity practitioners we already face hurdles getting our objectives met: we're a cost center, we have a reputation for standing in the way of business getting done, and we've had a bad run of luck as an industry in the recent past that could make even the most diehard supporters question the value of our function overall. Our credibility is all the more important because of this kind of reputation. If we're going to be effective at securing our organizations we must leave the performative theater behind and focus on being substantive, results oriented security leaders.

